This article is all about safeguard your Visual C# application from unauthorized copying
TABLE OF CONTENT
Introduction
Protecting any digital assets is prominent. As a developer, safeguarding the digital property from unauthorized copying is crucial to maintaining its integrity and value. unauthorized duplication leads to loss of revenue and increase the security risk.In this article we will discuss, How to avoid the unauthorized copying of an desktop application.
There are various ways to protect the user application like using Activation Keys by limiting users, Designing the login Panel to restrict the unauthorized users or using Online authentication. But in this article we will design a dummy application and restrict the authorized or unauthorized user from multiple copying by tracking the IP address of the authorized PC.
Process to Prevent the C# application
First of all, define the user’s IP address and allow the application to read the PC’s IP address. If the IP addresses match to the predefined ones, then allow the user to use your application; otherwise, show the message box with the message.
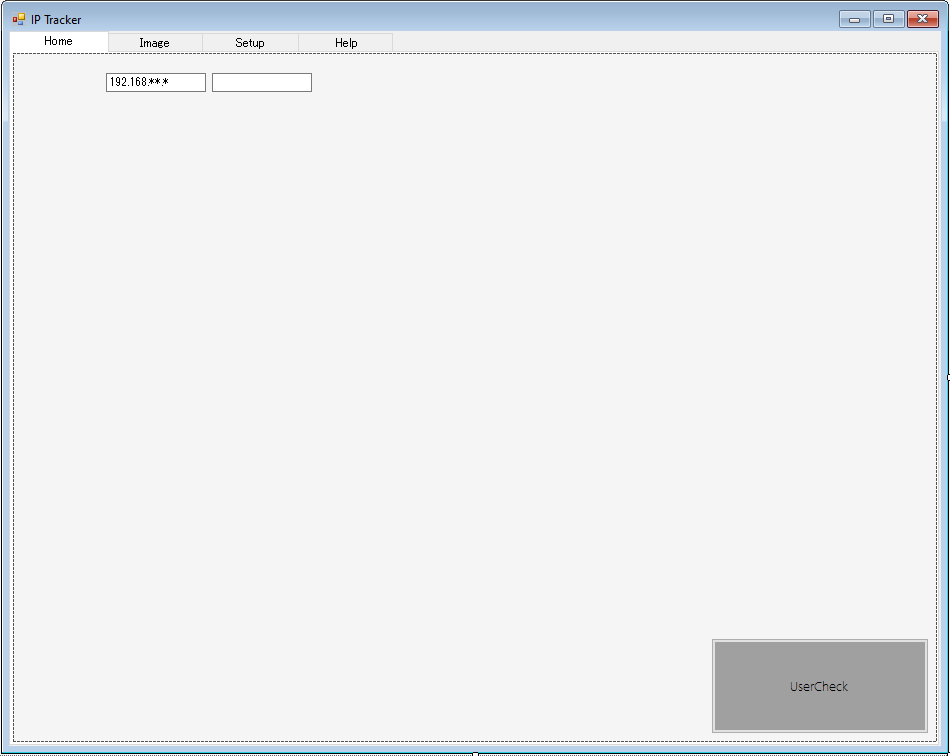
Let’s design the Windows application in Visual Studio. Add two textboxes, let’s say textBox1 and textBoxx2. In textBox1, the developer adds the IP address manually. In textBoxx2, the application reads the IP address. Then, if the text in textBox1 equals the text in textBoxx2, allow the user to use the application features; otherwise, display the warning message.
Also Read | C# App to Read/Write Switch PLC Bits
Application Code
using System.Net;
private string GetLocalIPAddress()
{
string localIP = "";
try
{
// Get the host name
string hostName = Dns.GetHostName();
// Get the IP addresses associated with the host
IPAddress[] localIPs = Dns.GetHostAddresses(hostName);
// Find the IPv4 address
foreach (IPAddress ip in localIPs)
{
if (ip.AddressFamily == System.Net.Sockets.AddressFamily.InterNetwork)
{
localIP = ip.ToString();
break;
}
}
}
catch (Exception ex)
{
MessageBox.Show("Error: " + ex.Message);
}
return localIP;
}
private void Form1_Load(object sender, EventArgs e)
{
string ipAddress = GetLocalIPAddress();
// Display the IP address in TextBoxx2
textBoxx2.Text = ipAddress;
}
private void button_Click(object sender, EventArgs e)
{
if (textBox1.Text == textBoxx2.Text)
{
MessageBox.Show("You are authorized user");
}
else
{
MessageBox.Show("you are not an authorized user \n" +
"consult to the Sales department ");
}
}Demonstration Videos
Now you can share your application by adding customers IP address so, that you can restrict the multiple copying of your digital assets.
Pros and Cons
| Pros | cons |
| Enhanced Security | Limited Effectiveness |
| Monitoring and Logging | Potential for False Positives |
| Controlled Access | Complexity and Maintenance |
You can also restrict your application from being copied multiple times by tracking the MAC address. This approach would be more efficient for the program developer.
Code to abstract The MAC ADDRESS
private string GetLocalMACAddress()
{
string localMAC = "";
try
{
// Get the network interfaces
NetworkInterface[] interfaces = NetworkInterface.GetAllNetworkInterfaces();
// Find the MAC address of the first non-loopback, operational network interface
foreach (NetworkInterface nic in interfaces)
{
if (nic.NetworkInterfaceType != NetworkInterfaceType.Loopback && nic.OperationalStatus == OperationalStatus.Up)
{
localMAC = nic.GetPhysicalAddress().ToString();
break;
}
}
}
catch (Exception ex)
{
MessageBox.Show("Error: " + ex.Message);
}
return localMAC;
}
private void Form1_Load(object sender, EventArgs e)
{
string MacAddress = GetLocalMACAddress();
// Display the IP address in TextBoxx2
textBoxx2.Text = MacAddress;
}



Discussion (0)
Share Your Thoughts